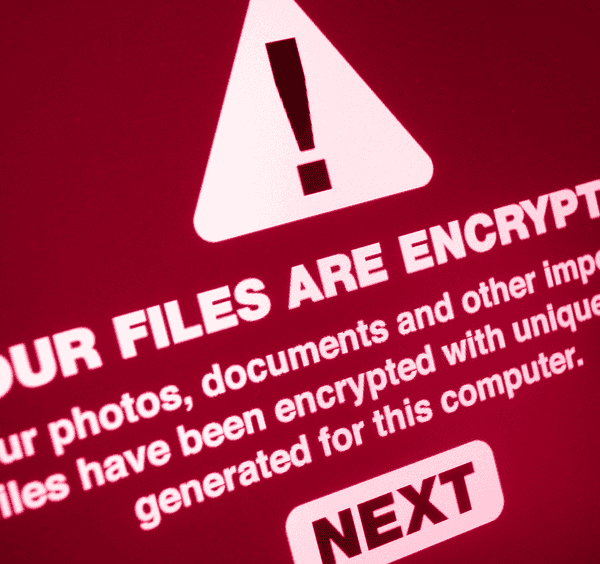
If your system is not in a great area, it can trigger a person to utilize ransomware to strike your system as well as hold you for ransom money. Your information is your company and also it is really essential that you do every little thing within your powers that […]
Blog
Wireless Access Point Audits
Due to the growing need for wireless networks and smartphones everywhere wireless networks have become the main target for cybercrime. The idea behind building a wireless network system is to provide easy access to users, but this may become an opened door to attackers. Many wireless access points are infrequently if ever updated.
Consulting Services
Cyber Security Consulting Ops provides consulting services in the following areas.
Unified Threat Management, Enterprise Security Solutions, Threat Detection & Prevention, Cyber Threat Protection, Threat Protection, and Network Security. Cyber Security Consulting Ops works with small and large businesses and homeowners. We fully understand the scope of the threat landscape which is growing every day. Regular Antivirus is not sufficient anymore.
Ransomware Protection
Ransomware is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. In recent months, ransomware has dominated the headlines, but incidents among the Nation’s state, local, tribal, and territorial (SLTT) government entities and critical infrastructure organizations have been growing for years.
Malicious actors continue to adapt their ransomware tactics over time. Federal agencies remain vigilant in maintaining awareness of ransomware attacks and associated tactics, techniques, and procedures across the country and around the world.
Here are A Few Ransomware Prevention Best Practices:
Conduct regular vulnerability scanning to identify and address vulnerabilities, especially those on internet-facing devices, to limit the attack surface.
Create, maintain, and exercise a basic cyber incident response plan and an associated communications plan that includes response and notification procedures for a ransomware incident.
Ensure devices are properly configured and that security features are enabled. For example, disable ports and protocols that are not being used for a business purpose.
Employees Training
Employees are your eyes and ears in your organization. Every device they use, emails they receive, programs they open may contain some types of malicious codes or viruses in the form of Phishing, Spoofing, Whaling/Business Email Compromise (BEC), Spam, Key Loggers, Zero-Day Exploits, or some type of Social Engineering Attacks. For companies to mobilize their employees as a force against these attacks, they offer all employees cyber security awareness training. These cyber awareness training should go well beyond sending employees simulated phishing emails. They must understand what they are protecting and the role they are playing in keeping their organization safe.
Make Data Driven Decisions
Data should be the key to making more informed, strategic cybersecurity decisions — and ensuring you are spending your security dollars effectively. To get the most out of your increasingly limited cyber security resources and meet or surpass industry benchmarks, you need visibility into the relative performance of your security program — and insight into the cyber risk present across your ecosystem. Your policies should be in place and up to date before a data breach. Your mindset set should be when, not if we get breached. The process needed to recover from a breach should be practiced daily, weekly, and monthly.
Used Our Cyber Resources
Most organizations lack the resources needed to maintain a robust cyber security compliance process. They either lack the financial backings or the human resources it takes to implement a robust cyber security system that will keep their assets safe. We can consult and evaluate your organization on what is needed to implement your cyber security processes and a robust system.
Reduce Your Hygiene Risk
What is good cyber security hygiene?
Cyber hygiene is compared to personal hygiene.
Much like, an individual engages in certain personal hygiene practices to maintain good health and well-being, cyber hygiene practices can keep data safe and well-protected. In turn, this aids in maintaining properly functioning devices by protecting them from outside attacks, such as malware, which can hinder the functionality and performance of the devices. Cyber hygiene relates to the practices and precautions users take intending to keep sensitive data organized, safe, and secure from theft and outside attacks.
Block The Attack Paths
-Constant IT education
-Update known vulnerabilities
-Segmentation of your internal networks
-Constant employees awareness training
-Phishing test for all employees and CEO’s
-Fix all known vulnerabilities on your website
-Fix all known vulnerabilities on your external network
-Monthly, Quarterly cyber security assessments based on your industry
-Continues conversation about the impact of a cyber breach with your employees
-Let employees understand it is not a single person responsibility but the entire team
Block Attacks Paths
We specialize in cybersecurity solutions as a solution supplier to help your organization block attacks paths before hackers can get to them. We use cybersecurity analysis solutions, IT Assistance Providers, Wireless Infiltration Screening, Wireless Accessibility Factor Audits, Internet Application Evaluations, 24 × 7 Cyber Tracking Solutions, HIPAA Conformity Analyses, PCI […]