Blog
Industries Experiencing The Highest Cyber Incidents Rate
Not surprising, healthcare is on top of the hackers list. Why? Because there’s lots of personal information available and most medical offices are depending on detached IT security companies that are using computer policies to protect major holes in their business network. This list is from IBM Security.
Business Cyber Attacks On The Rise
Business Cyber attacks are on the rise. According to top Cyber security companies Cyber attacks are rising fast. Business Cyber Attacks Top 4,000 Per Day: Our Cyber Security Consulting Company serve customers in all fifty (50) states. We can help your business remotely or get someone onsite to harden your […]
Phrases Used To Describe Cyber Security Threats
Theses are all the names that help to identify cyber security threats in today’s threat landscape. The is simply too vast and complex to rely on a single, silver bullet solution. Successful information security management requires a broad mix of technology, strategy, processes, people and information security services – all aligned with business objectives to ensure operational success. The Cyber Operations is a wide field that have many areas of interest both technical and non technical areas. Malware – Malware includes any software that harms a system, data, or processes/applications. Trojan – Trojans hide in applications to get into a user’s system or they act as a program themselves. This malware does not replicate. Spyware – This malware gathers a user’s private data (financial info, passwords, usernames, etc.) and sends it to the spyware maker. Adware – Software that displays ads is considered adware. Not all adware is bad. Worms – A computer worm is a replicating program that spreads to other computers. Most rely on networks for transportation. Viruses – Computer viruses are replicating code that spread by hiding inside of infected applications and installers. Zombies – Computer zombies are computers that are controlled by a malicious hacker or computer virus to complete malicious tasks. Riskware – Software with unintended malicious potential. These applications can be used by malware to cause a lot of damage. DDoS Cyber Attack Protection – Prevent attackers from using un-wanted request to drain resources on server or website .
Cyber Crime News Update
No one is immune from becoming a victim of cyber crime. It’s important to understand the daily threats landscape and stay up-to-date on the latest cyber crime news.
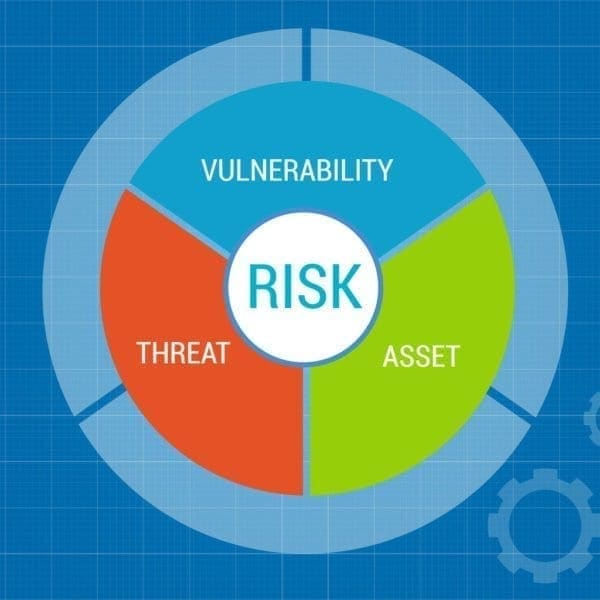
Vulnerability Assessment
Why It’s Important To Run Vulnerability Assessment Test On Your Network! find a company that can give them an assessment of their business and home network. There is a serious Cyber war raging for your assets and we must do all we can and more than we can to protect it. So many times we hear about identity theft and for the most part we assume it cannot happen to us while we are on our home or small business networks. This is the furthest thing from the truth. There are millions of vulnerable routers and other devices that thieves can login to everyday. Most consumers are not aware of this. The assumptions are, when they purchase a router or firewall application it’s safe and there’s nothing else to be done. This is absolutely the furthest thing from the truth. All devices MUST be upgrade as soon as a newer firmware or software is available. It’s a possibility the new firmware release was to patch an exploits.
Intrusion Detection Systems
highlighted new trends for 2015 where hackers are causing major disruptions. They are disrupting business, stealing personally identifiable information and attacking routers and switches. I believe this new trend will continue into the foreseeable future. This is where Cyber Security Consulting Ops can help your home or business network to implement a good detection strategies can help to detect un-wanted visitors on your system. We MUST shift our focus to both prevention and detection. Intrusion Detection can be defined as “…the act of detecting actions that attempt to compromise the confidentiality, integrity or availability of a resource.” More specifically, the goal of intrusion detection is to identify entities attempting to subvert in-place security controls. Asset Must be use as bait to entice and track bad entities for early warning.
End Point Protection
The End Point Protection is a technical term refer to the client’s technologies we used to protect your laptop, desktop, smart phones, tablets and other smart devices or devices that fall under the term Internet of Everything (IoT). These devices uses firmware or can be updated to fix vulnerabilities. The EPP is the technology installed on the aforementioned devices to protect them from hackers or those with intentions of doing us harm. There are numerous technologies like virus and malware protections that can be considered as EPP. Traditionally people and organization mistakenly spend too much effort on protecting the perimeter which in this case could be firewall protection, but very small amount of resources on End Point Protection. Too much resource spend on the perimeter is a poor return on your investment. Because of this type of security we get the coconut protection. Hard on the outside, but soft on the inside. This is where Cyber Security Consulting Ops can help you to protect your entire network to include all your End Point clients. Today Cyber Security has to have defense in depth. The coconut security concept is tremendously flawed. To better protect your assets you must have a layered security approach. It should be like a tough onion. To get to the middle a hacker must have to work hard to get to your asset.
Federal, State & Other Memberships
Is Your System Safe? Take The Free Analysis Test Here!
, you may never find out. The truth of the matter is most individuals and organizations may never find out until the hackers are gone.